Phishing emails come in all shapes and sizes. Exhibit 2 – “Response” is an example of a simple looking request with potentially devastating consequences.
Emails such as these target individuals, not companies. Known as “Gift Card Scams“, they want gift cards and will ask for the codes needed to redeem them. When the victim seeks reimbursement from the individual or company that was impersonated, they end up out of luck as the request was a scam.
Let’s get to it.
The Phish!
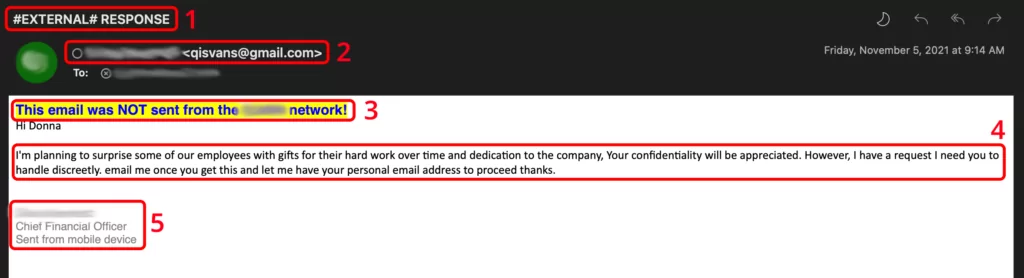
Exhibit 2 uses several techniques to trick a target into acting and evading detection.
Indicator 1 – Subject Line

The first indicator from this sample is the subject. Many organizations include “tags”, such as #EXTERNAL# in subject lines. This is to help employees identify emails coming outside the company. External messages should be treated with caution.
Another indicator here is what follows this #EXTERNAL#. Vague or generic subjects, or those not matching the body or tone of an email can be an indicator of malicious intentions.
Indicator 2 – From/Sender Address

Looking at the sender address can often be the only clue you need.
Ask yourself if you recognize the email address. If not, proceed with caution.
Another indicator with sender addresses is a “free” address, such as Gmail, Hotmail, or another service. Be careful with emails from free services that look like they are coming from someone you work with.
Indicator 3 – Warning Banner

Many businesses include warning banners on emails from outside the company network. As such, be vigilant when you see these. Some attackers will try to fool you with fake “safe sender” banners.
Indicator 4 – Secrecy/Call to Action

The nature of a request can often be all you need to spot a phish. Here is what smells funny:
- Involving you emotionally
- Missing and misplaced capital letters and punctuation
- Requests to be discreet, or keep the request secret
- Attempting to change the communication to a personal email address
Emotions are powerful. Human nature is innately good. We want to help. The message conveys the message that hard workers are going to be rewarded. Deep down, we all wish to be recognized and rewarded for our hard work.
Secrecy is a technique used by attackers to isolate a victim. Often an unbiased opinion can spot a phish. By isolating you with a secret task, the attacker limits who can detect their ruse.
Any time you receive a request that wants to change the method of communication, you must be wary. Switching from email to text or a messaging app, or any change is suspicious. Why not contact you with that method in the first place? By moving off your company email address, the attacker prevents the company tools from detecting their deception in future messages.
Indicator 5 – Email Signature
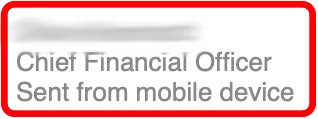
Email signatures can provide clues as well. In this example, the “Sent from mobile device” does not read as proper English. Does the signature match the company standard? Does it look out of place or odd for the person the message claims to be from? Most people don’t include their work title on a personal email address.
Never trust the information in an email you aren’t certain of. Call the person the email claims to be from using a number you know for them, or can locate in your company directory. That ensures you aren’t calling the attacker using a number they control.
Summary
Time to wrap up!
In Exhibit 2, the following indicators can be found that the email may not be trustworthy.
- A subject line showing the email is from outside the company
- The From/sender address is not from the company address
- Your company displays a warning banner
- Poor spelling/grammar
- Emotional involvement
- Secrecy
- A call to action
- An out of place email signature
Trust your instincts when reading email. Exhibit 2 – “Response” is a common scam. If an email smells funny, it probably is. Ask a colleague or your IT department if you aren’t sure. With personal accounts, ask a friend or family member for input.










