The first inductee into Kalnara’s Hall of Phish is a familiar trick. Learn how to spot bad emails in Exhibit 1 – “Expiration of user accounts!”.
The Phish!
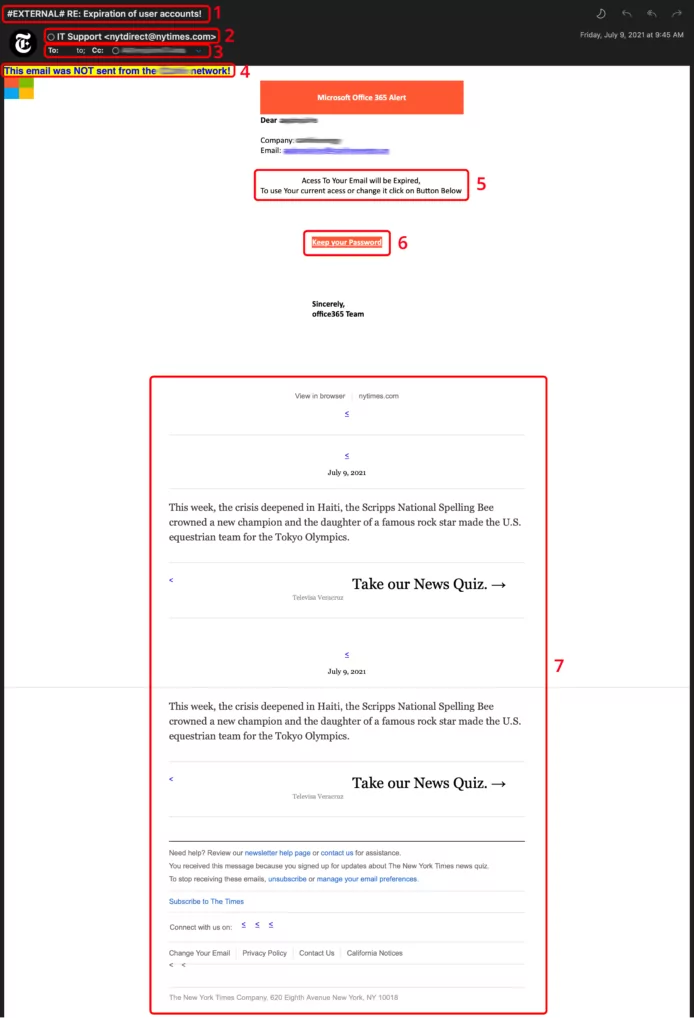
This sample uses several tricks, including spam filter evasion and a forged “From” address.
Indicator 1 – Subject Line

Many companies add a tag, or short piece of text, to the subject line of emails received from outside the organization. In this example, the tag #EXTERNAL# has been added to raise the suspicion level of the email.
Emails from outside sources are less trustworthy than those coming from someone within an organization. If your organization does this, it is an easy way for you to know you need to start off wary.
Indicator 2 – From/Sender Address

The From/Sender address in this example does not line up with the message body. Microsoft would not send any notifications from the NY Times. Additionally, the NY Times is not likely to send emails to their customers from “IT Support”.
Emails regarding account expirations usually come from “noreply” or other addresses that do not accept replies.
Indicator 3 – To/CC Lines

Look at the “To” and “CC” lines. There is valid no entry in the “To” field. This is a red flag.
A reputable email will be addressed to your email address, using the “To” field, not “CC” or “BCC”.
Indicator 4 – Warning Banner

This helpful banner is commonly added to emails coming into businesses. It is one more reminder to be cautious about the email you are looking at.
Beware, though! Attackers have begun adding their own banners to trick you! Know what your company uses or ask someone in IT if you aren’t sure.
Indicator 5 – Urgency/Call to Action
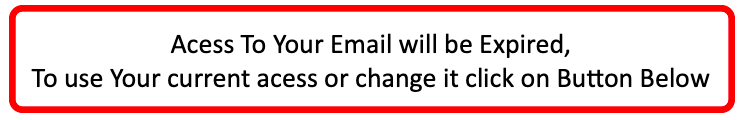
The top trick used by successful social engineers is a sense of urgency.
Take a step back and read this clue again. Such wording, albeit with a poor grasp of English, instills the fear of losing something. In this case, your access.
By tricking your brain into “fight or flight mode”, the attacker is trying to override your ability to think critically. They are counting on the fear you feel to prompt you to click before you realize something is wrong.
If you are pressed to do something immediately to avoid missing out, stop. Someone is manipulating you to take an action that is in someone else’s best interest, not yours.
Indicator 6 – Strange Looking Link

By hovering your mouse over the link or button, you will see the destination for the link. Do you recognize it? You can view links without clicking on phones or tablets by long-pressing on the link. Be careful, however; it is easy to accidentally click.
Many businesses use services to send emails and track what you click. These emails often hide the true website address behind a tracking link. This is done so the sender can see who clicks different links, but this can be used by an attacker.
If you aren’t sure about a notification, open your web browser and go directly to the website and login. This is the safest way to change an expiring password.
One more thing – reputable services won’t ask you to “keep” your current password. If anything, they’ll force you to change it next time you login.
Indicator 7 – Out of Place Content/Information
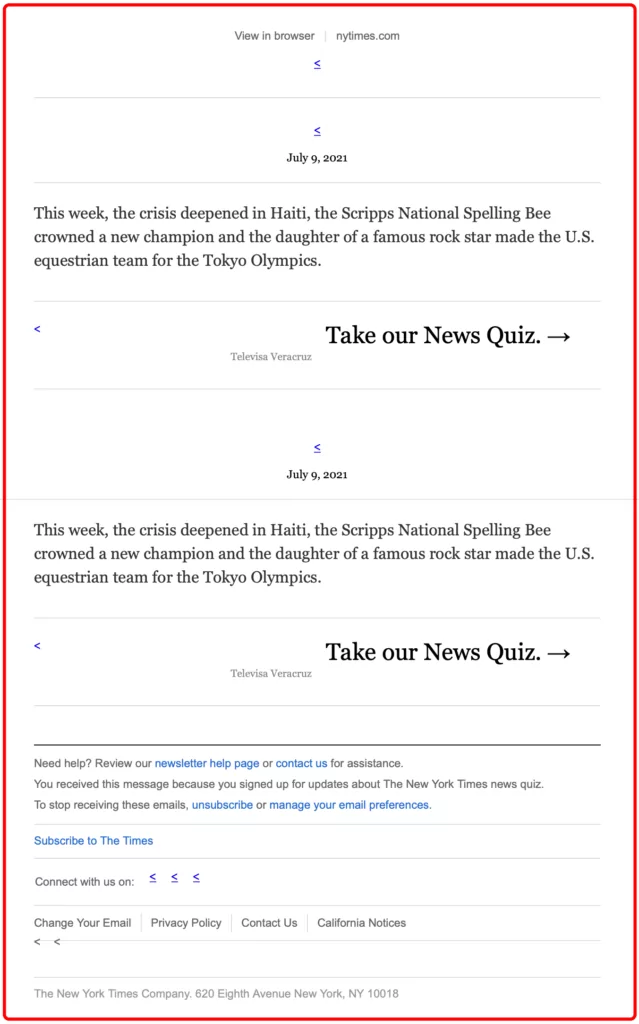
Attackers use this technique to trick email filters into thinking a message is safe. It works by “stuffing” or “padding” the email with legitimate looking information. By doing this, the attacker makes the email look less suspicious to the automated systems that scan email.
Imagine looking at a picture with 5 dots. 4 of those dots are red (bad) and one dot is blue (good).
How would you describe it? Perhaps you would describe a picture of mostly red (bad) dots.
Now think if there were still only 4 red (bad) dots, but 100 blue dots.
How would you describe the picture now?
Attackers use the same logic to hide the malicious intentions of emails with this technique.
If you see an email titled “Expiration of user accounts” detailing news stories of the day, this is a warning sign.
Summary
Every phish is unique. Exhibit 1 – “Expiration of user accounts!” shows how your logical thinking could be overridden by the fear of having your account locked.
The clues we examined together are:
- A subject line showing the email is from outside the company
- The From/sender address that doesn’t match the email body topic
- The To/CC field does not contain your email address
- Your company displays a warning banner
- Poor spelling/grammar
- A link that looks strange
- Extra information or content that is out of place










